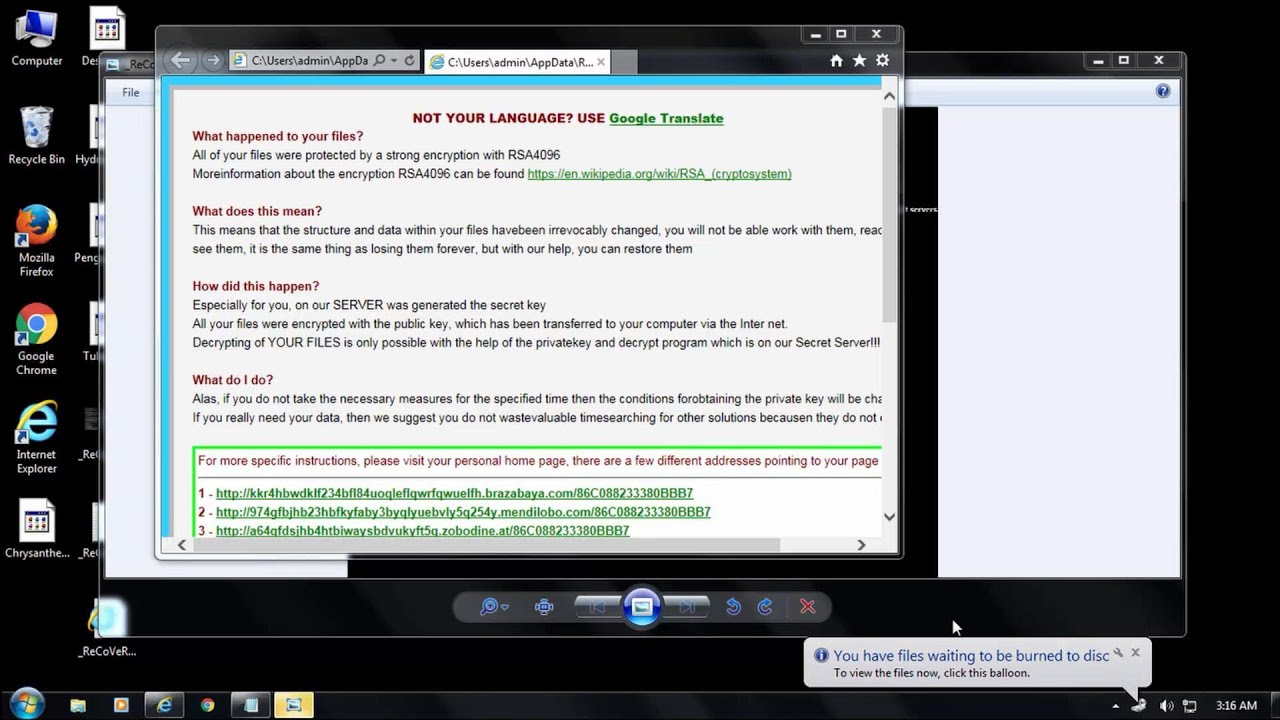
My husband’s PC which is running Windows 7 had a message popup saying that an RSA4096Key was installed and all files were encrypted with the public key which has been transferred to your computer via the internet. You have to obtain BITCOIN in order to unencrypt your files at a cost. Can’t get rid of it and can’t get into anything on computer.
Pay the ransom, or restore from backup.
ETA: assuming that your files are really encrypted, and it’s not some obnoxious “fake” ransomeware.
No telling if your message is for realz or just a prank, but there have been cases of this happening for realz. Malware infects your computer; encrypts or otherwise locks you out of all your files; demands payment of a ransom to get your data back.
It happened to a hospital, where all their medical records and other similar critical data got hijacked and held for ransom. The hospital ended up paying $17,000 to get their data back.
Hollywood Hospital Pays $17,000 Ransom to Hacker for Unlocking Medical Records
ETA: And, scumbags who do this shit being scumbags, no guarantees either that, even if you pay the ransom, they’ll give you your data back.
It is called ransom-ware. He clicked on a link which installed malware.
Read the stickies the ATMB about how to remove.
Plus there are procedures now on how to recover, but might involve a computer-savy person to help you. Google/Bing are your friend. Search the forums here on Ransomware. I hope you have a recovery disk. You will lose your data.
Get MalwareBytes, an antivirus program, keep them up-to-date, update Windows or hire me for $250 USD per hour.
Oh. and keep him off the porn-sites. ![]()
The versions I’ve seen encrypt MS Office files (doc, docx, xls(x), etc.) and jpg (photo) files. I have yet to hear of any solution. If you’ve been infected, you can run Malwarebytes or Trend Housecall to do a deep inspection; may have to download the Malwarebytes from another compuer. Then install one of the free Anti-Virus like AVG… if you are lucky. No backup typically means you’ve lost it all…
An alternative is to wipe the computer and re-install. (Some newer computers come with a “restore to factory default” option on the hard disk, others with a CD that does thinks. This is what we typically do since you have no idea what is lingering on the Windows install otherwise.
Most such infections come from email nowadays, not bad websites. Be very careful what attachments you open.
The virus is easy to remove via Malwarebytes. The problem is that by the time you learn you have it, the files are encrypted.
Without a backup, there’s not much you can do. Even if you pay the ransom, there’s a good chance it’ won’t work, and the cure may just add more malware.
Run a Malwarbytes scan to get rid of the virus, then restore from backup.
Backups are essential these days. You should install Mozy on all your computers, and save files in Dropbox (which has versioning, so you can get back the older files). It’s too late for that, of course, but once you clean up the mess, this will help you recover if it happens again.
You have two options
-
pay the ransom;
-
don’t pay the ransom
If you pay the ransom, there is absolutely no guarantee that you will get a key to decrypt your files or that you wont be held to ransom again in the near future.
If you don’t pay the ransom, you either have to remove the ransomware (a quick google search leads to a number of sites with detailed removal steps), or restore your PC from backup, which may lead to a loss of data. If you’re not comfortable with either of these steps, get a tech savvy friend to have a look or take it to a PC technician.
No promises, but most ransomware has pretty good “customer service”. They need to maintain a reputation for delivering as promised if they get the money, because no one will pay them in future if they don’t.
I had a client who got hit by an encryption malware. By the time he called me, his encrypted files had already been backed up to Carbonite, so when I restored the backup files, they were encrypted also. Fortunately, when I contacted Carbonite, they were able to go back before the malware struck and retrieve a previous backup. All was restored. Carbonite was awesome.
Just one thing to add… ransom ware tends to encrypt all attached storage devices, so a backup won’t help if it’s on a locally connected USB drive or similar. I realise this doesn’t help the OP, but I just thought I’d mention it as general info.
Sent from my iPhone using Tapatalk
Note: A few ransomware programs have been cracked and people are able to get their files back.
The OP might be very lucky and be encrypted by one of those. (Ransomware people tend to continue to use broken systems since few people are aware of it being broken.)
The trick is trying to find out which ransomware program it is and if it’s been cracked.
An AV program might be able to provide a name for that and Googling might help. Also try searching for the exact message contents.
Here’s an example of one that was recently cracked.
Excellent point. I backup once a week. Once I heard about ransomware, I now precede the backup with a reboot. After the backup, I copy the backup to a external drive and disconnect the external drive before I start any applications. The next week, I use a different external drive. I copy all user files to another computer every two days. Am I paranoid? yes, but when I was hit with an obnoxious virus last fall, it took me a day to recover. It wasn’t ransomware, but I couldn’t get rid of it, so I reloaded. I’m so paranoid, that I keep a recent bakup at my sister’s house in case my house burns down.
I can’t say that this is a global possibility but have read somewhere - probably The Register, that if you run another encryptor on the encrypted files it returns them to plain text.
You might try copying a few files and trying it. If it works it saves you the ransom and you can give them the finger, if it fails you are no worse off - as long as it is only copied files you use it on.
I got one of those a while back. Linux just laughed at it 
This strikes me as exceedingly unlikely.
FWIW porn sites are not the major vector for viruses anymore. You still can get viruses at some porn sites but the reality is church websites are the most dangerous to visit now.
That’s why it’s good to have a backup solution with versioning. That allows you to restore any version of the file from backup.
Dropbox has automatic versioning, so you can get the good versions back even if the encrypted ones have been uploaded. It’s time consuming, but far less time than recreating the files.
I have no been involved in half a dozen of these infections in the last few months 2 of which have paid their ransom and got all their files back.
The annoying part was every file now looked like “Decrypted_filename.xxx” and still left the encrypted ones behind. So there is a not insignificant cleanup after the ransom is paid.
Spent a while learning how to batch edit file names in powershell to get that sorted.
2 of the others were customers of my offsite backup service and we just deleted everything and restored the backups, worked perfectly.
The big threats now are the Petya ransomware that encrypts entire drives. Bare metal backups will now become more critical than ever especially for small businesses that might require several days to manually restore software and configuration. ddropbox and carbonite will not save you here.
I hope they fired their IT department. It’s one thing for a home user to be running without a back up strategy in place but a hospital is pretty much the very definition of “mission critical.”
Rumor has it there was a backup strategy and system in place however there was an issue with those backups.
So it wasn’t that they lacked a parachute, but that the chute malfunctioned when deployed.