Nowadays, I expect they just flame each other on twitter.
Which does just what other posters warned about – this told the Egyptians that an Israeli counter-attack was coming.
(Whether they made good use of that info, or whether it was pretty obvious from the start, is a different matter.)
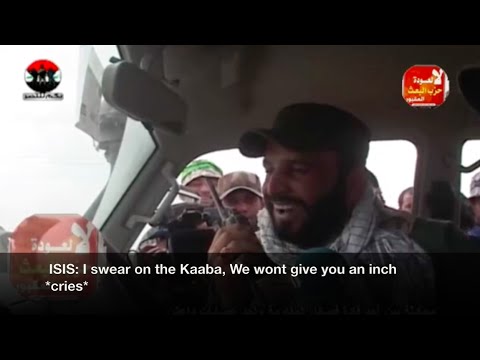
Here is video of a Shia Militiaman taunting a member of ISIS using a captured radio. This seems to be a recent example of what the OP is referring to.
I’ve read that during World War II some American troops could have compromised the Navajo “Code Talkers” program. Hearing a language that they didn’t recognize, they decided it was the Japanese enemy, so some American GIs tried to jam the transmissions by breaking in. This caused the code talkers to have to explain, over the air in English (which some of the Japanese troops understood), that they were American, and they may have also stated that they were speaking Navajo, which would have given any Japanese listening in a better idea of what language was being used. Fortunately, Japan didn’t have any native Navajo speakers.
The RAF during WW II also used native German speakers to try and misdirect night fighter pilots by giving false course information for intercepts. However, a number of the operators usually just wound up screaming curses at the Germans, so jamming was substituted instead.
The jamming was done by aircraft known as Airborne Cigars, or ABC aircraft.
If the enemy does capture a radio, how does the military deal with that in terms of operational security? In very short and one-sided wars like Gulf War I, US radios must have been pretty safe but in other wars, it wouldn’t be that surprising for some US radios to fall into enemy hands.
Without the secret magic codes and the secret machinery to insert them into the radios, they become useless bricks in a matter of a few hours.
To be sure the radios can be sent back to the enemy’s reverse engineering directorate. Assuming they have one. The Russians and Chinese certainly do. The Grenadans, Panamanians, Iraqis, and Afghans, not so much. Ditto the narco-traffickers & Somali pirates.
One of the central tenets of modern security design is to assume the enemy has your gear and understands how it works. The protection lies in them not being able to pull today’s code out of a freshly captured machine, and not being able to predict tomorrow’s code no matter what they capture.
What is the source of this information?
Certainly true of SINCGARS when I played with them in 1996. I have to imagine the current incarnation can see an individual unit deliberately bricked immediately if it is thought to be compromised.
This mirrors the instruction we were given in the event WE were captured. Basically: “Destroy the gear and info if you have the time & means, and cooperate with your interrogators and keep yourself and companions safe. If you’re captured we’re going to assume you’ve told all you know, and provided excellent instructions about operating the gear.” We were operators, not tough guys.
Because of this, it’s generally accepted that any intel you have is useless within 24 hours. The trick is not trying NOT to break (resulting in injury and maiming), but instead trying to talk around the main nugget long enough for either the event to happen, or the plan to change.
I don’t remember where I read the original article, but I found a couple of similar cases.
From Code Talkers Story Pops Up Everywhere in the October 11, 1999 New York Times: more than once, code talkers were briefly mistaken for Japanese soldiers by their American comrades.
Sometimes the similarities had almost comic consequences, as when Paul H. Blatchford, a code talker from Fort Defiance, Ariz., was mistaken for Japanese by an enemy soldier who heard him on the radio in Iwo Jima.
''He said, ‘Where are you from?’ ‘’ recalled Mr. Blatchford, an electrical engineer who at 82 is the oldest surviving code talker. ''He said, ‘Talk English,’ and he thought we were Japanese. One of my buddies heard me and he said, ‘What the hell are you talking about?’ I lied and told the Japanese guy that the Japanese artillery was not hitting our guns, and said, ‘Tell your guy to move about 15 degrees to the east.’ ‘’
From the book “Code Talker”: "As part of the training, those men arranged to put some of us on shipboard–both submarine and surface ships–and some on land. We often spread out like this for field maneuvers aimed at practicing the code.
“Someone not involved with our group heard the messages, and all along the California coast troops suddenly went to ‘condition black’ (a state of readiness where weapons were prepared for immediate use) thinking that the Japanese had invaded the United States mainland at San Diego. A couple of the code talkers were taken to North Island Headquarters, where they quelled the panic. They listened to the tapes of ‘Japanese’ made by the officers and identified the language as Navajo. One of the colonels involved with the program told his superiors that the strange language was their own Navajo Marines speaking a code they had developed. He promised to give headquarters advance warning so the Navajo words wouldn’t be mistaken for Japanese and wouldn’t cause panic”.
In his book “The Wild Blue: the Men and Boys who flew the B-24s over Germany 1944-45” Stephen Ambrose says on one mission a German-speaking American radio operator got on a German radio channel and got the fighter pilots to return to base by pretending to be the squadron base commander.